Breakout Testing
Comprehensive Citrix Security Assessments

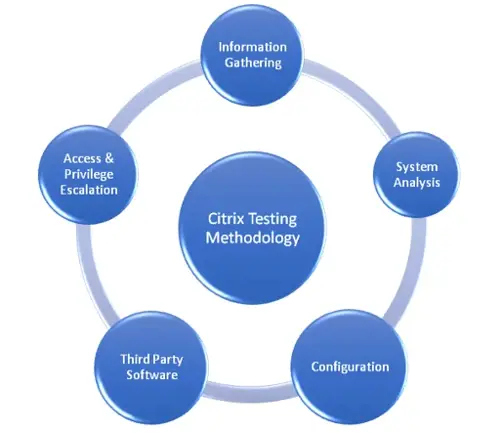
Citrix solutions provide robust, secure program access for remote users. Yet, without a comprehensive assessment of configurations, permissions, and implementations, vulnerabilities may exist. Overly generous user privileges could enable unintended program executions and unauthorized access to file systems, potentially compromising the broader network.
Citrix Security Assessments By ProCheckUp
At ProCheckUp, we specialise in meticulous Citrix Security Assessments and remote desktop PenTesting, leveraging cutting-edge security testing tools. Our approach is holistic, fusing our deep expertise in Citrix vulnerability analysis with methodologies from network infrastructure and web application domains.
Remote desktop solutions, including Citrix and Microsoft Terminal Services, are critical for secure remote access. However, misconfigurations can inadvertently grant excessive access rights to users.
We conduct targeted assessments for Citrix environments using contemporary security tools and developmental frameworks. Our tests encompass:
- Black Box Assessments: without system knowledge.
- Grey Box Assessments: with provided client credentials but no system knowledge.
- White Box Assessments: Comprehensive assessments with full knowledge of the system and its configurations
Drawing from our vast experience, we pinpoint security gaps within the environment. Potential vulnerabilities include:
- Citrix Security Assessments: Detection of flaws allowing users to circumvent published applications.
- Privilege Escalation: Evaluating the potential for users to gain heightened permissions.
- Insecure Programs: Identifying programs with weak configurations that may be exploited.
- Credential Security: Investigating for insecurely stored access credentials.
- Authentication: Scrutinizing the robustness of authentication processes and adherence to strong password policies.
- Data Transmission: Monitoring remote session traffic, with prior agreement, to uncover potential security gaps.
Before commencing a Citrix Security Assessment, we undertake a detailed scoping exercise. While we refrain from using tools that might induce a Denial of Service (DoS) situation, penetration tests could generate atypical traffic, potentially affecting network functionality. We ensure immediate communication lines during any testing phase for prompt pausing or cessation if required.
Post-assessment, we furnish an in-depth report, securely delivered to designated recipients. Our reports adhere to the format stipulated in Section 4 and are crafted at our offices..
Network Breakout/Pivoting
Why do you need a Network Breakout PenTest?
Going beyond typical red team testing is adversarial simulation. Here, consultants mirror actual attackers, leveraging their TTPs to evaluate the efficacy of client security mechanisms against genuine threats. These evaluations can be enriched with threat intelligence to understand client-specific risks better.
Unlike a basic penetration test aiming to unearth and exploit vulnerabilities, a red team evaluation confirms the readiness of security instruments and personnel in detecting and thwarting attacks.
ProCheckUp's expertise spans years, and using tried-and-tested techniques, we unearth potential security flaws. Our methodology aligns with the Bank of England’s standards, encompassing:
- Reconnaissance: Gathering crucial background data about the target. This phase leverages reports from our esteemed Threat Intelligence Partner, Digital Shadows.
- Staging: Post-reconnaissance, we set up platforms mirroring designated threat actors to simulate attacks.
- Exploitation: Leveraging known tactics to exploit discovered vulnerabilities and gain unauthorized entry.
- Control and Movement: Post a successful breach, we simulate attempts to access other systems, demonstrating potential risks.
- Actions on Target: Accessing and retrieving agreed-upon target data, strictly within agreed parameters.
Persistence and Egress: Demonstrating how advanced attackers could maintain prolonged network access and perform data ex-filtration.
Any simulated data used is approved in advance by the client, ensuring full transparency and alignment.
Why Choose ProCheckUp for Your Cybersecurity Needs
Choosing ProCheckUp means partnering with a proven leader with over 25 years experience. Our CREST approval and NCSC endorsements reflect our commitment to delivering top-tier cyber services across various sectors. We offer flexible, cost-effective solutions tailored to meet the diverse needs and budgets of our clients, ensuring continuous improvement.


For More Information Please Contact Us

ACCREDITATIONS






