Healthcare Sector
Quick Introduction:
In an era where data breaches are becoming alarmingly routine, the healthcare sector faces uniquely critical cyber-security challenges. Healthcare records contain some of the most sensitive personal information, from medical histories to insurance details. As technology integrates deeper into the fabric of healthcare - from electronic health records to connected medical devices - the sector becomes a more lucrative target for cyber-criminals. The consequences of cyber-attacks in healthcare are particularly severe, potentially compromising patient privacy, disrupting care, and eroding trust in healthcare systems.
Protecting this vital sector requires an in-depth understanding of both the risks involved and the regulations in place to mitigate them. The UK’s healthcare institutions must navigate a complex landscape of cyber-security regulations to protect their patients’ data and ensure the continuity of their operations.
Cyber-security Regulations
NHS Data Security and Protection Toolkit
The NHS Data Security and Protection Toolkit is a set of standards for ensuring that patient information is handled securely. It is mandatory for all NHS organizations and those who hold NHS patient data.

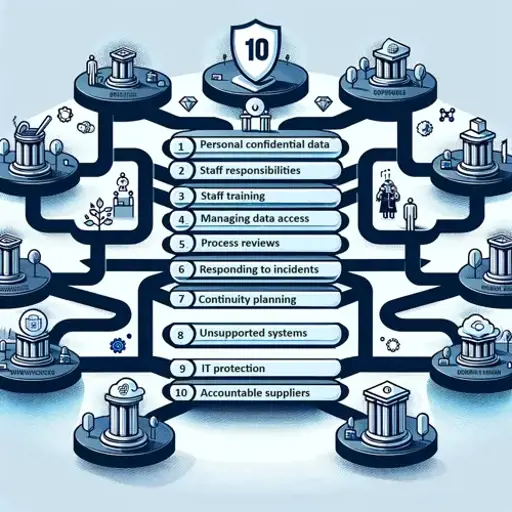
National Data Guardian’s (NDG) 10 Data Security Standards
All health and care organisations are expected to implement the 10 National Data Guardian (NDG) standards for data security. These standards are designed to protect sensitive data, and also protect critical services which may be affected by a disruption to critical IT systems (such as in the event of a cyber attack).
These standards provide a framework for handling patient data, addressing aspects such as leadership, consent, and data sharing. They apply to all organizations that handle health and care information.
UK-GDPR: Prioritizing Data Privacy in Healthcare
The UK General Data Protection Regulation (UK-GDPR) adapts the European Union’s stringent data protection rules to the UK post-Brexit. For healthcare providers, UK-GDPR means safeguarding patient data with the highest levels of security. Consent for personal data use is particularly sensitive in a medical context, requiring clear communication and stringent record-keeping.

Data Protection Act 2018
This act complements the UK-GDPR and provides specific guidelines for processing personal data. In healthcare, it impacts everything from patient records to staff information. Compliance ensures that healthcare providers respect privacy while maintaining high standards of patient care.

NIST Cybersecurity Framework
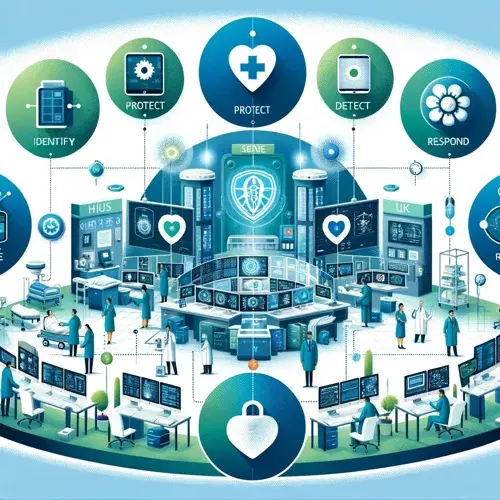
The US-based National Institute of Standards and Technology (NIST) provides a cyber-security framework widely respected worldwide. In the UK, healthcare providers often look to the NIST framework for guidance in developing comprehensive cyber-security policies and procedures. The core functions of the framework—Identify, Protect, Detect, Respond, and Recover—are particularly relevant to healthcare providers as they offer a systematic approach to managing patient data and medical devices securely.
Adopting the NIST framework helps UK healthcare organizations to:
- Identify critical assets and the potential risks to patient data and hospital operations.
- Protect services through access control, data security practices, and staff training.
- Detect cyber-security events promptly to reduce the potential impact on patient care.
- Respond to detected cyber-security events with a defined action plan to contain and mitigate damage.
- Recover from incidents effectively and restore any impaired services as quickly as possible.
PCI-DSS: Securing Cardholder Data
The Payment Card Industry Data Security Standard (PCI-DSS) is essential for healthcare providers that process card payments, whether for treatments, prescriptions, or insurance services. Compliance ensures that all cardholder data is secured against unauthorized access, reducing the risk of financial fraud.

COBIT (Control Objectives for Information and Related Technology)
COBIT is a framework for managing and governing enterprise IT, emphasizing regulatory compliance, risk management, and aligning IT strategy with organizational goals.

HIPAA (Health Insurance Portability and Accountability Act)
While not a UK regulation, HIPAA is a significant benchmark for global healthcare cyber-security standards. UK healthcare entities dealing with US patients or partners must ensure HIPAA compliance, which governs the protection and privacy of health information.
ISO27001
This is a widely recognized standard for information security management systems (ISMS), offering a systematic approach to managing sensitive company information to ensure it remains secure.
ProCheckUp Solution's
UK-GDPR Compliance:
- IASME Cyber Essentials: A certification that verifies basic cyber-security hygiene, ensuring that Healthcare institutions have fundamental security controls in place to protect against common cyber threats. (Learn More)
- IASME Cyber Assurance: This includes a GDPR readiness assessment to ensure that all aspects of data privacy and security are addressed, thus aligning with the GDPR’s stringent requirements.(Learn More)

For Data Protection Act 2018 Adherence:
- Data Protection Impact Assessments (DPIA): Services to help Healthcare institutions conduct assessments that evaluate the impact of new projects or technologies on the privacy and security of personal data.(Learn More)
- Data Governance Consulting: Expert consultancy to ensure the correct handling of personal data across all operations, aligning with the Data Protection Act’s provisions.

For PCI-DSS Compliance:
- PCI-ASV (Approved Scanning Vendor) Services: ProCheckup, a globally recognized ASV, conducts meticulous external vulnerability scans to ensure the integrity of systems handling credit card data, in compliance with PCI-DSS requirement 11.3.2. Our ASV scan solution leverages cutting-edge security tools to rigorously test and confirm your network's defenses against known threats, helping to secure your data transactions. (Learn More)
- PCI-QSA (Qualified Security Assessor) Services: As an independent QSA firm accredited by the PCI Security Standards Council, ProCheckup embodies excellence in ensuring entities meet the stringent standards of PCI DSS. Our longstanding expertise, since the establishment of the QSA program, provides reliable validation of your compliance posture. (Learn More)
- Penetration Testing: ProCheckup's penetration testing services are an embodiment of our commitment to security excellence, meeting PCI-DSS requirement 11.4.1. Our team of Crest, Cyberscheme, and NCSC-qualified penetration testers, with a proven 24-year track record since 1999, employs a comprehensive approach to identify and remediate exploitable security vulnerabilities. (Learn More)
- Data Discovery for Primary Account Number (PAN): Our specialized services extend to the detection of PAN within your network, particularly identifying unauthorized storage locations outside the Cardholder Data Environment (CDE), adhering to PCI-DSS requirement 12.5.2. ProCheckup ensures that sensitive payment data is contained and managed securely. (Learn More)
- Segmentation Testing: With precise technical testing, ProCheckUp validates the efficacy of network segmentation, ensuring that the CDE is isolated from all systems not pertinent to card processing , in compliance with PCI-DSS requirement 11.4.5 This critical service supports PCI-DSS compliance by verifying the robustness of segmentation controls, maintaining the security of your cardholder data environment. (Learn More)
- Wireless Testing: Adhering to the stringent standards of PCI-DSS requirement 11.2.1, our team conducts comprehensive wireless testing quarterly. This process is meticulously designed to uncover and assess both sanctioned and unsanctioned wireless access points within your network, ensuring a robust security posture. (Learn More)

For ISO27001 Compliance:
- ISO 27001 is the international standard outlining best practices for an information security management system (ISMS). In the digital age, ensuring the security, integrity, and confidentiality of corporate information is paramount. ISO 27001 certification demonstrates an organization's commitment to this end (Learn More)
By integrating these cyber-security services,Healthcare institutions can effectively navigate the complexity of regulatory compliance while fortifying their defenses against the cyber threats that endanger the sector’s integrity and stability. These services provide a scaffold for building a comprehensive cyber-security strategy that is not just about adherence to the letter of the law but also about embedding cyber-security into the fabric of Healthcare services operations.
Maintaining Compliance
Top Cybersecurity Solutions for the Healthcare Sector
Cyber-security in healthcare is not just about compliance; it's about safeguarding the welfare of patients and the integrity of the healthcare system. The following solutions are vital in establishing a robust defense against cyber threats:
- Access Control Systems: These systems are essential for regulating who can view and edit sensitive patient information.
- Advanced Threat Protection: Utilizing AI and machine learning to detect and respond to novel threats promptly.
- Encryption and Data Loss Prevention: To ensure that patient data, both at rest and in transit, is unreadable to unauthorized individuals.
- Mobile Device Management (MDM): Given the rise of telehealth and mobile health applications, MDM ensures that mobile platforms are secure.
- Network Segmentation: Separating critical medical devices and patient data from the main network to limit the spread of potential breaches.
- Security Information and Event Management (SIEM): For real-time analysis and alerts on potential security incidents.
- Regular Security Assessments and Training: Continuous assessments, including penetration testing and employee training programs, help maintain high-security standards.
- Incident Response Plan: A well-prepared response plan that is regularly updated and rehearsed is crucial for minimizing the damage from cyber incidents.

Cybersecurity Process Flow Chart
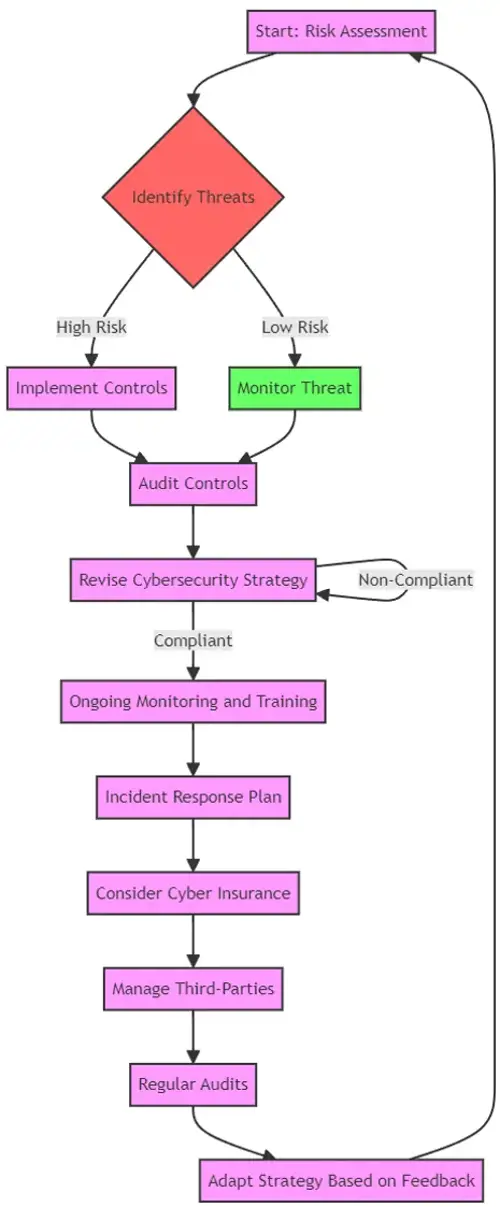
Cybersecurity Collaboration and Sharing
In addition to the internal measures, it is crucial for Healthcare services to actively participate in sector-wide cyber-security initiatives. These include:
- Regulatory Engagement: Maintaining an open dialogue with regulators to stay ahead of new regulations and to influence policy development with real-world insights.
- Public-Private Partnerships: Partnering with government agencies to enhance the collective cybersecurity posture and respond more effectively to national security threats.
- Global Cybersecurity Standards: Aligning with global cybersecurity standards and frameworks, such as ISO/IEC 27001, to ensure a consistent approach to managing information security.
- Cybersecurity Advocacy: Advocating for stronger cybersecurity measures and more substantial investments in cyber-security at industry conferences and in public forums.
For More Information Please Contact Us

ACCREDITATIONS






