What is Penetration Testing?
Penetration testing, commonly referred to as a pen test, is a simulated cyber attack against a computer environment where security experts attempt to find and exploit vulnerabilities. .
Table of Contents
- What is Penetration Testing?
- What Are The Types Of Penetration Tests?
- Types Of Advanced Penetration Testing
- What Are The Penetration Test Approaches?
- What Are The Penetration Testing Stages?
- What Are The Benefits of Penetration Testing?
- What Are The Challenges In Penetration Testing?
- What Are The Ethical Considerations?
- Selecting a Penetration Testing Vendor
- What Are The Common Types Of Penetration Tests?
- Common Questions
- Conclusion
What Are The Types Of Penetration Tests?
Penetration testing, or pen testing, involves a range of techniques aimed at identifying and exploiting vulnerabilities in network systems and applications to improve their security. This section explores the different types of penetration tests.
External Network Testing
Targets the assets of the company that are visible on the internet, for instance, the company website, email and domain name servers (DNS).
Internal Network Testing
Simulates an internal threat. This test is crucial to understanding what an attacker could do once inside the perimeter defenses.
Web Application Testing
Specifically targets web applications and looks for security flaws in them, like Cross-Site Scripting, SQL Injection, and more.
Wireless Security Testing
Focuses on the wireless networks within the organization, identifying access points and testing their security, including encryption and password policies.
Social Engineering Testing
Involves attempts to coerce or trick employees into revealing sensitive information that could be used for unauthorized access.

Types Of Advanced Penetration Testing
Red Teaming
A multi-layered attack simulation that tests how well an organization's people, networks, applications, and physical security controls can withstand an attack from a real-life adversary.
A.I. Based Penetration Testing
Use of A.I. based software to simulate cyber-attacks against computer systems to find and create exploitable vulnerabilities, complementing manual testing efforts.

What Are The Penetration Test Approaches?
There are different approaches to penetration testing, including Black Box, White Box, and Grey Box testing..
Black Box Testing
The tester has no prior knowledge of the network infrastructure. This simulates an attack from an outsider's perspective.
White Box Testing
The tester has full knowledge of the network infrastructure, providing a comprehensive evaluation of internal and external vulnerabilities.
Grey Box Testing
Partial knowledge of the system is provided, offering a balanced view of how an insider might exploit the system.
What Are The Penetration Testing Stages?
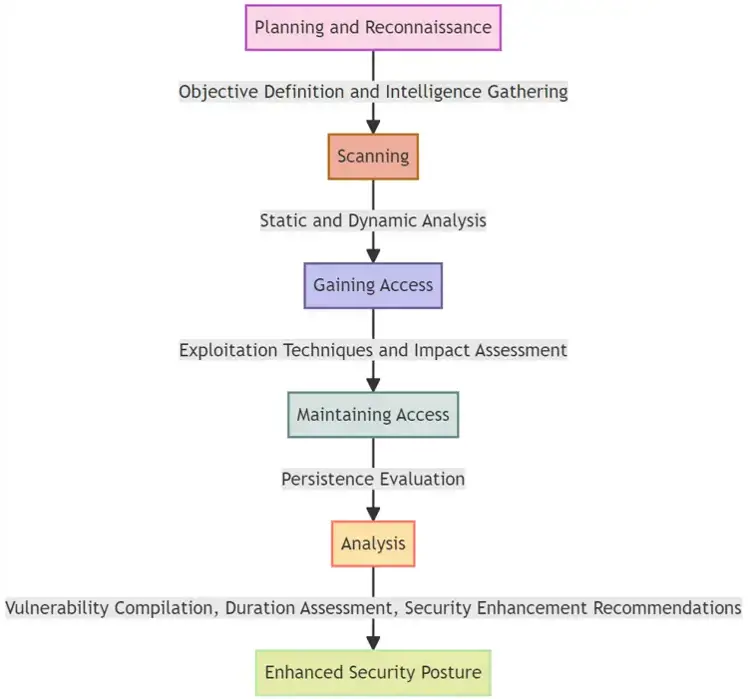
What Are The Benefits Of Penetration Testing?
Penetration testing offers numerous benefits that are crucial for maintaining the integrity and functionality of organisational IT systems:
- Proactive Security: By simulating attacks, organisations can identify and address security vulnerabilities proactively before they are exploited by malicious entities.
- Risk Management: Penetration testing helps prioritise the remediation of vulnerabilities, allowing organisations to focus resources on critical issues that could have the most severe impact on their operations
- Testing Cyber-Defense Capability: Regular testing ensures that an organisation's security measures remain effective in the face of evolving cyber threats.
- Compliance with Regulatory Standards: Penetration testing helps in adhering to compliance standards like PCI-DSS, HIPAA, or GDPR, which require evidence of robust security practices.
- Protect Customer Trust and Company Image: By identifying and fixing vulnerabilities before they are exploited, companies protect their reputation and maintain customer trust.
- Reducing Network Downtime: By preventing attacks that can cause network outages, penetration testing helps maintain operational continuity and avoids the costs associated with downtime and recovery.
- Training Opportunities: Penetration tests also serve as training exercises, improving the skills of security teams and preparing them to effectively handle potential breaches.
What Are The Challenges In Penetration Testing?
Despite its benefits, penetration testing presents several challenges that organisations need to manage effectively:
- Evolving Security Threats: Continuously changing attack vectors demand that pen testers stay updated with the latest hacking techniques and tools.
- Resource Intensity: Penetration testing can be resource-intensive, requiring significant time and skilled personnel, which might be challenging for organizations with limited cyber-security budgets.
- Balancing Depth with Scope: Determining the appropriate depth of testing while keeping within the scope to ensure a thorough assessment without overstepping boundaries.
- Potential Disruption: Although rare, penetration testing can inadvertently affect production environments if not carefully controlled, leading to disruptions in services and operations.
- False Positives and Negatives: Managing the balance between false positives and negatives in test results requires expertise to ensure that security teams are not overwhelmed by misleading information or overlook critical vulnerabilities.

What Are The Ethical Considerations?
Penetration testing must be conducted with strict adherence to ethical standards to prevent legal issues and maintain the trust of stakeholders:
- Consent and Legal Compliance:Penetration testing should be conducted only with explicit permission and within legal boundaries.
- Scope Agreement: Clearly define and agree on the scope of the penetration testing to avoid accessing or testing systems not covered under the authorization.
- Responsible Disclosure:Any vulnerabilities found during testing should be confidentially disclosed to the organization for them to address.
- Data Handling:Secure handling of any data obtained during testing to prevent leakage or misuse.
- Non-Disclosure: Penetration testers should agree to non-disclosure terms to protect the organization's sensitive information.
- Impact Minimisation: Conduct tests in a manner that minimises the impact on the operational environment to avoid disrupting normal business processes.
- Professional Conduct: Testers must conduct themselves professionally, avoiding any actions that could be interpreted as malicious.
Selecting a Penetration Testing Vendor
When choosing a vendor for penetration testing, consider:
- Expertise and Reputation: Look for providers with a proven track record and certified professionals.
- Customized Testing Plans: Ensure the vendor offers testing plans tailored to your specific environment and business needs.
- Post-Test Support: Opt for vendors who provide comprehensive reports and actionable insights, along with follow-up support to address vulnerabilities.

What Are The Common Types Of Penetration Tests?
Network Penetration Testing
Network penetration testing is a critical cyber-security practice aimed at evaluating the security of a network's infrastructure. It simulates a cyber attack against a network to identify vulnerabilities and security issues that malicious hackers could exploit. This type of testing is crucial for any organization to protect its data and resources from external and internal threats.

Key Components of Network Penetration Testing
- Scope and Planning: Defining the scope of the penetration test, including which systems, networks, and devices will be tested.
- Establishing the goals and objectives of the penetration test (e.g., identifying vulnerabilities, testing network performance under stress).
- Reconnaissance: Gathering information about the target network through passive and active reconnaissance methods. Identifying IP ranges, domain details, network services, and potential entry points.
- Vulnerability Assessment: Scanning the network using automated tools to identify known vulnerabilities.Classifying and prioritizing vulnerabilities based on severity and impact.
- Attempting to exploit identified vulnerabilities: to gain unauthorized access or gather sensitive information. Demonstrating the potential impact of an exploit, such as data theft, unauthorized access, or service disruption.
- Post-Exploitation Analysis:Determining the level of access gained.Identifying any additional network vulnerabilities or data exfiltration opportunities.
- Reporting and Recommendations: Documenting the findings, including a description of the vulnerabilities, the exploitation methods used, and the potential impact. Providing recommendations for mitigating the identified risks and vulnerabilities.
- Remediation and Re-Testing: Assisting with remediation efforts based on the penetration test findings.
Performing re-testing to ensure that vulnerabilities have been effectively addressed.
Challenges in Network Penetration Testing
- Evolving Network Architectures: Adapting to complex and dynamic network architectures, including cloud-based and hybrid networks.
- Advanced Security Measures: Overcoming sophisticated security controls like firewalls, intrusion detection systems, and anomaly detection mechanisms.
- Ensuring Business Continuity: Conducting tests without disrupting normal business operations and network services.

Tools Commonly Used
- Vulnerability Scanners: Tools like Nessus, OpenVAS for automated vulnerability discovery.
- Network Mappers: Tools such as Nmap for discovering devices and services on a network.
- Exploitation Frameworks: Metasploit or similar frameworks for exploiting vulnerabilities.
Best Practices
- Conduct Regular Testing: Regularly schedule network penetration tests to identify and address new vulnerabilities.
- Comprehensive Scope: Ensure a comprehensive test scope that includes all aspects of the network infrastructure.
- Ethical Approach: Always conduct testing within legal boundaries and with proper authorization.
Network penetration testing is a vital part of an organization's overall security strategy, offering insights into the security posture of the network infrastructure. By identifying and addressing vulnerabilities, organizations can significantly reduce their risk of cyber attacks and data breaches.
Web Application Penetration Testing
Web application penetration testing is a specialized type of security testing specifically focused on evaluating the security of web applications. The primary goal is to identify and exploit vulnerabilities in web applications to assess the risk posed by malicious attacks. This process is vital for organizations to safeguard their web applications against potential cyber threats.

Key Components of Web Application Penetration Testing
- Scope Definition: Clearly defining the scope of the penetration test, including targeted web applications and functionalities. Determining testing boundaries, such as authenticated vs. unauthenticated areas.
- Information Gathering:Performing reconnaissance to gather information about the application, server, and associated technologies. Identifying entry points and potential areas of weakness (e.g., input fields, authentication processes).
- Vulnerability Assessment: Using automated tools and manual techniques to scan for common web application vulnerabilities, such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF). Analyzing the application’s responses to various inputs and attack vectors.
- Exploitation: Attempting to exploit identified vulnerabilities to determine their impact. Demonstrating how a malicious actor could leverage these vulnerabilities.
- Business Logic Testing: Testing the application’s business logic to identify logic flaws that can be exploited.
Assessing the application's ability to handle unexpected or malicious input. - Reporting and Recommendations:Documenting identified vulnerabilities, exploitation methods, and potential impact on the application.Providing detailed remediation recommendations for each identified vulnerability.
- Remediation and Re-Testing :Assisting in the remediation process based on the findings.Performing re-testing to ensure vulnerabilities are resolved.
Challenges in Web Application Penetration Testing
- Complex Application Logic:Understanding and testing complex business logic unique to each web application.
- Evolving Technologies: Keeping up with rapidly evolving web technologies and frameworks.
- False Positives and Negatives: Distinguishing between true vulnerabilities and false positives/negatives in automated scanning results.
Commonly Used Tools
- Vulnerability Scanners: Tools like OWASP ZAP, Burp Suite for automated vulnerability scanning.
- Proxy Tools: Intercepting proxies such as Burp Suite or Fiddler to analyze and manipulate web traffic.
- Exploitation Tools: Tools or frameworks to exploit specific vulnerabilities, like SQLmap for SQL injection.
Best Practices
- Ethical Hacking: Ensure testing is conducted ethically and legally with proper authorization.
- Regular Testing: Conduct penetration tests regularly, especially after significant changes to the application.
- Comprehensive Coverage: Test all aspects of the web application, including client-side, server-side, and API components.
Web application penetration testing is crucial for identifying security weaknesses in web applications before they can be exploited by attackers. It involves a combination of automated and manual testing techniques to provide a comprehensive assessment of the application's security posture.
Cloud Penetration Testing
Cloud penetration testing, especially for platforms like Azure and AWS, is a critical cyber-security practice designed to identify and exploit vulnerabilities within cloud environments. Given the complexity and shared responsibility model of cloud services, this form of testing is essential for ensuring cloud infrastructure's security and resilience.

Key Components of Cloud Penetration Testing
- Understanding Cloud Architecture: Familiarization with Azure and AWS architectures, including services like EC2, S3, Azure VMs, and Blob Storage. Recognizing the unique security challenges posed by these platforms, such as mis-configured storage buckets or virtual networks.
- Scope Definition and Permissions: Clearly defining the scope of testing in agreement with cloud service providers' policies. Obtaining necessary permissions to conduct tests, as unauthorized testing can violate terms of service.
- Testing Methodologies: Employing methodologies tailored to cloud environments, focusing on both infrastructure as a service (IaaS) and platform as a service (PaaS) models.
Identifying mis-configurations, inadequate access controls, and improper use of cloud-native features. - Vulnerability Assessment: Using automated tools to scan for vulnerabilities specific to cloud services.
Checking for exposed data, insecure APIs, and potential entry points for attacks. - Exploitation: Attempting to exploit identified vulnerabilities while ensuring no disruption to cloud services.
Simulating real-world attack scenarios to evaluate the impact on cloud resources. - Compliance and Best Practices: Ensuring compliance with industry standards and best practices for cloud security, such as CIS Benchmarks for AWS and Azure. Assessing alignment with frameworks like NIST and ISO standards.
- Reporting and Remediation:Providing detailed reports on findings with actionable remediation steps.
Offering guidance on enhancing cloud security postures and implementing robust security controls.
Challenges in Cloud Penetration Testing
- Cloud Complexity: Navigating the complexities of Azure and AWS services and configurations.
- Rapid Evolution: Keeping pace with the rapidly evolving cloud services and features.
- Service Limits: Recognizing and respecting the service limits imposed by cloud providers.
Tools for Cloud Penetration Testing
- Automated Scanners: Tools like Nessus or Qualys, configured for cloud environments.
- Cloud-Specific Tools: AWS Inspector, Azure Security Center, and third-party tools designed for cloud platforms.
- Manual Testing Techniques: Custom scripts and methodologies for deeper inspection of cloud-specific vulnerabilities.
Best Practices for Cloud Penetration Testing
- Pre-Testing Consultation: Engaging with cloud providers to understand boundaries and legal implications.
- Continuous Monitoring: Implementing continuous monitoring solutions to detect and respond to threats in real-time.
- Security Training: Educating teams about cloud-specific security practices and common pitfalls.
Cloud penetration testing requires a comprehensive approach that considers the unique aspects of cloud services, legal and compliance issues, and the dynamic nature of cloud environments. Proper execution of cloud penetration tests ensures that organisations can leverage cloud capabilities securely and efficiently.
Common Questions
Penetration Testing is a critical component of cyber-security, with various aspects often misunderstood. Below are some commonly asked questions to provide clarity on its purpose and how it is executed.
1. What is Penetration Testing in Cyber-security?
Answer: Penetration testing, also known as a pen test, is a method used in cyber-security where security experts simulate cyber attacks against a system to identify and exploit vulnerabilities. This proactive measure helps organisations strengthen their defenses against actual cyber threats.
2. How Does Penetration Testing Differ from Vulnerability Scanning?
Answer: While vulnerability scanning involves using automated tools to identify potential vulnerabilities in a system, penetration testing is more comprehensive. It not only identifies vulnerabilities but also attempts to exploit them in a controlled environment to understand the real-world effectiveness of existing security measures..
3. What Types of Penetration Tests are There?
Answer: There are several types of penetration tests including, but not limited to, external network testing, internal network testing, web application testing, and wireless security testing. Each type targets specific aspects of an organisation’s IT infrastructure.
4. Who Should Consider Penetration Testing?
Answer: Any organisation that handles sensitive data or relies on IT infrastructure for their operations should consider penetration testing. It is particularly crucial for sectors such as finance, healthcare, education, and government, where data breaches can have severe consequences.
5. What Skills are Required for a Penetration Tester?
Answer: Penetration testers typically need a broad range of skills in cybersecurity, including knowledge of network systems, proficiency with penetration testing tools and techniques, and often, skills in programming and script-writing. Critical thinking and problem-solving skills are also essential..
6. How Often Should Penetration Tests Be Conducted?
Answer: The frequency of penetration tests can vary based on several factors such as the size of the organisation, the nature and sensitivity of the data handled, and the changing threat landscape. Generally, it is recommended to conduct penetration tests annually or biannually, or after any significant changes to the IT infrastructure or deployment of new systems..
7. What are the Ethical Considerations in Penetration Testing?
Answer: Ethical considerations in penetration testing include obtaining explicit permission from the rightful owners or stakeholders before testing begins, ensuring the testing is legal, respecting privacy laws, and avoiding any actions that could disrupt the normal operations of the system being tested.
Conclusion
Effective penetration testing is integral to an organisation's cyber-security strategy. It provides valuable insights into vulnerabilities and defensive capabilities, empowering businesses to fortify their security posture against evolving cyber threats.
For More Information Please Contact Us

ACCREDITATIONS






