Secure Build and Configuration Review Services
In today's intricate digital ecosystems, the proper configuration of workstations and servers is paramount. Ensuring these devices adhere to recognized best practices and security benchmarks not only bolsters cybersecurity but can also be a significant line of defense against threats.

The ProCheckUp Advantage:
Harnessing the benchmarks laid out by esteemed entities such as the Center for Internet Security (CIS), ProCheckUp offers meticulous build review services. Particularly for organizations employing standard builds across various departments, ensuring these builds are secure is non-negotiable.
Our extensive experience spans diverse environments, from Unix and Windows servers to various database setups. Typically integrated into on-site infrastructure assessments, our reviews guarantee a comprehensive scrutiny of your configurations.
Our Comprehensive Review Methodology:
To promise uniformity and rigor in our reviews, we've distilled a proprietary methodology. At its core, this methodology guarantees that areas like firewall rule sets and configurations are rigorously evaluated.
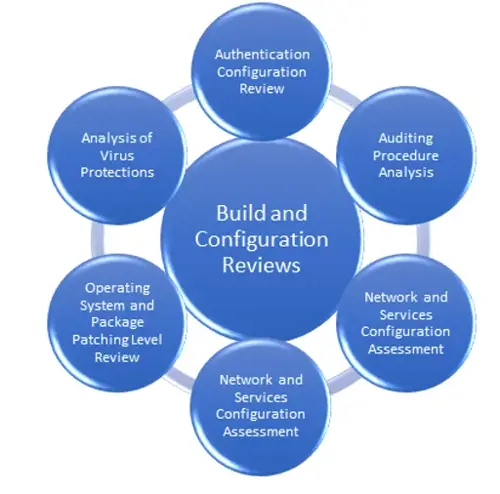
Diving Deeper into Firewall Ruleset and Configuration:
Unlike our suite of penetration tests, our firewall reviews adopt a narrative-centric approach. With configurations and, when feasible, network diagrams supplied by clients, we conduct an exhaustive "step-through" evaluation. This scrutiny extends to the device's Access Control List(s) and associated configurations. Our reports flag any deviations from established best practices, including over-extended permissions, reliance on frail protocols, outdated firmware, or inadequate logging protocols.
A thorough combing of the firewall's Access Control Lists (ACL's) ensures only essential accesses, aligned with the organization's functional needs, are granted.
Beyond Firewalls – Network Device Reviews:
In complement to our firewall evaluations, ProCheckUp delves into the configurations of other network devices. From switches and routers to load balancer's, we leave no stone unturned.

For More Information Please Contact Us

ACCREDITATIONS






