Developing A SME Cybersecurity Policy

In today's digital age, the importance of cyber-security for small and medium-sized enterprises (SMEs) cannot be overstated. With cyber threats becoming more sophisticated, it's crucial for businesses, especially those in the UK where digital business operations are foundational, to establish and maintain robust cyber-security defenses. This guide aims to walk you through the process of developing and implementing an effective cyber-security policy for your SME.
The Importance of Having a Formal Cyber-security Policy
A formal cyber-security policy serves as the foundation of your company's defense against cyber threats. It outlines your approach to managing and protecting information assets, thereby reducing the risk of cyber attacks. In the UK, where SMEs are increasingly targeted by cyber-criminals, having a cyber-security policy is not just recommended; it's essential for survival. A thoughtfully devised policy can help prevent data breaches, protect company reputation, and ensure business continuity.
The Five Pillars Of An Effective Cyber-security Policy
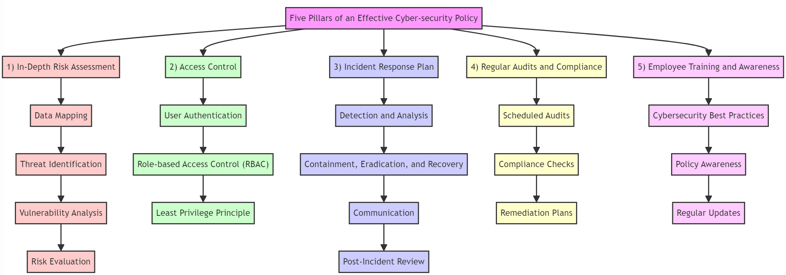
Pillar 1 - In-Depth Risk Assessment
A comprehensive risk assessment is the bedrock upon which a cyber-security policy is built. It provides a clear picture of the potential risks facing an organisation's IT infrastructure, guiding the development of a robust cyber-security strategy. This section delves deeper into the four critical stages of the risk assessment process: Data Mapping, Threat Identification, Vulnerability Analysis, and Risk Evaluation.
Data Mapping
The journey begins with data mapping, a critical process where you catalogue all data your organisation handles, especially focusing on sensitive and critical data susceptible to cyber threats. This step goes beyond mere listing; it's about understanding how data flows through your organization, identifying where it’s stored, and evaluating the security measures in place to protect it. This thorough analysis lays the groundwork for a solid cyber security framework by highlighting what needs protection and where the major vulnerabilities might lie:-
- Identify Data Types: Start by identifying different types of data, such as personal data, financial records, intellectual property, and any other information that could be valuable to attackers.
- Map Data Flow: Trace how data moves within and outside your organisation. Understand how data is collected, stored, processed, and disposed of. This includes both digital pathways and physical movements, such as data transferred via USB drives or printed documents.
- Identify Storage Locations: Pinpoint exactly where sensitive data is stored across your network, including on-premises servers, cloud storage, employee devices, and third-party services.
- Assess Data Protection Measures: Evaluate the current security measures in place to protect sensitive data at each point in its life-cycle, from encryption practices to access controls.
- Classification: Classify data based on sensitivity and the impact of unauthorised access or loss, guiding the level of protection required.
Threat Identification
Next, we identify potential threats, from malware and phishing to insider threats and beyond. This stage is not just about listing potential dangers; it's about understanding the specific threats relevant to your industry and technology infrastructure. By staying informed about both current and emerging cyber threats, you can better prepare and protect your organisation against them:-
- Catalog Potential Threats: List potential cyber threats, including malware attacks, phishing schemes, ransomware, insider threats, and physical security breaches.
- Industry and Technology Specific Threats: Consider threats specific to your industry or sector. For example, financial institutions may be more susceptible to sophisticated phishing attacks, while retail businesses might face higher risks of POS system breaches. Include threats that target your particular technology infrastructure.
- Emerging Threats: Stay informed about emerging cyber threats by following cyber-security news, attending industry conferences, and participating in relevant forums.
Vulnerability Analysis
Here, the focus shifts to using advanced tools and techniques for identifying system weaknesses that could be exploited by attackers. This involves conducting regular vulnerability scans and penetration tests to uncover security gaps, including outdated software, unpatched systems, and misconfigurations. Additionally, the security of third-party services and the supply chain is assessed, acknowledging that vulnerabilities in these areas can directly impact your organisation.-:
- Vulnerability Scanning: Use vulnerability scanning tools to automate the process of identifying weaknesses in your network, including outdated software, unpatched systems, and misconfigurations.
- Penetration Testing: Consider engaging in penetration testing, where ethical hackers simulate attacks on your systems to identify vulnerabilities and test the effectiveness of your security measures.
- Third-Party Services and Supply Chain Review: Assess the security practices of third-party vendors and supply chains, as their vulnerabilities could also affect your organisation.
Risk Evaluation and Prioritisation
Finally, evaluate and prioritise risks based on the potential impact and likelihood of occurrence. This step is crucial for focusing your cyber-security efforts where they are needed most, ensuring an effective allocation of resources towards mitigating the highest-priority risks.
- Impact Analysis: Determine the potential impact of each identified risk on your organisation, considering factors such as financial loss, reputational damage, and operational disruption.
- Likelihood Assessment: Assess the likelihood of each risk occurring, taking into account the current threat landscape and the effectiveness of existing security measures.
- Prioritise Risks: Use the impact and likelihood assessments to prioritise risks, focusing remediation efforts on those that pose the greatest threat to your organisation
Patch Management, Firewalls, Malware Protection, and Secure Configuration
By integrating critical cyber-security aspects such as system updates, firewalls, malware protection, and secure configurations into their risk assessment, SMEs can enhance their security measures and prepare more effectively against cyber threats.
System Updates (Patch Management)
- Vulnerability Analysis: Regular system updates and patch management are crucial for mitigating vulnerabilities. Incorporate a systematic approach to regularly update and patch systems as part of your
- vulnerability analysis. This strategy should highlight the necessity of keeping all software and systems up to date to protect against known exploits and vulnerabilities.
- Routine Patch Management Strategy: Establish a routine patch management protocol as a dedicated section within your cybersecurity policy. Utilize automated tools where possible to ensure that software updates and patches are applied promptly, reducing the risk window for cyber-attacks.
Firewalls
- Firewall Configuration: Firewalls serve as a primary defense mechanism against unauthorized access. In the risk assessment process, evaluate the effectiveness of your firewall configurations. This includes assessing rulesets, verifying that firewalls are correctly configured to deny unauthorized traffic, and ensuring proper segmentation of networks.
- Best Practices for Firewall Management: Develop guidelines for managing and monitoring firewall configurations effectively. This should cover the implementation of a default-deny rule, regular audits of firewall rules, and the utilization of next-generation firewalls for enhanced security capabilities.
Malware Protection
- Anti-Malware Strategies: Malware protection is fundamental to a comprehensive cyber-security policy. Within the risk assessment, emphasize the importance of implementing robust anti-malware solutions that offer real-time scanning, threat detection, and removal capabilities.
- Regular Scanning and Real-time Protection: Focus on strategies for continuous monitoring and protection against malware. This includes regular scans of all systems, real-time threat detection, and the use of up-to-date anti-malware software to prevent infections.
Secure Configuration
- Secure System Configurations: The initial configuration of systems and devices significantly impacts their security posture. Include a thorough review of secure configurations in your risk assessment, emphasizing the need to harden systems against attacks. This involves disabling unnecessary services, closing unused network ports, and changing default credentials.
- Guidelines for Secure Configuration: Provide a set of standards and practices for securely configuring hardware and software within the organization. Refer to industry best practices and compliance frameworks to guide these configurations, ensuring that systems are set up to minimize exposure to threats.
Implementation Guidelines:
- Cross-Functional Collaboration: Engage stakeholders from various departments — IT, legal, finance, operations — to ensure a comprehensive risk assessment.
- Dynamic Review Process: Treat risk assessment as an ongoing process, regularly updating it to reflect new information, emerging threats, business changes, and technological advancements.
- Documentation and Communication: Keep detailed records of your risk assessment findings, methodologies, and decisions. This documentation is vital for regulatory compliance, internal audits, and informed decision-making.
By meticulously conducting each stage of the risk assessment process, organisations can develop a clear understanding of their cyber-security posture, enabling them to craft a cyber-security policy that addresses their specific vulnerabilities and threats. This proactive approach is essential for protecting sensitive data and ensuring the resilience of the organisation against cyber attacks.
Pillar 2 - Access Control
Access control is a fundamental aspect of cyber-security, dictating how users interact with an organisation's resources. It encompasses everything from physical access to buildings to digital access to computer networks and data. In the realm of cyber-security, effective access control measures are essential for protecting sensitive information from unauthorised access, ensuring that only those with a legitimate need can view, modify, or delete data.This pillar is intricately linked to the core aspects of updating systems, configuring firewalls, malware protection, and secure system configurations, ensuring a robust defense mechanism against potential cyber threats.

Steps to Implement Robust Access Control:-
- Identify and Categorise Data and Systems: Begin by identifying what data and systems need protection. Categorise these based on sensitivity and the potential impact of unauthorised access. This categorisation will guide the level of access control required.
- Define Access Requirements: For each category of data and system, define who needs access and for what purposes. This step involves mapping out job roles and their corresponding data access needs to ensure employees have only the access necessary to perform their duties.
- Implement Role-Based Access Control (RBAC): RBAC is a method of restricting system access to authorised users. It's simpler to manage and audit than managing individual user permissions because users are assigned roles based on their job functions with predefined access privileges to systems and data.
- Deploy Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring two or more verification factors, which significantly decreases the risk of unauthorised access. Implement MFA for accessing sensitive systems and data, especially for remote access scenarios.
- Regular Access Reviews: Conduct regular reviews and audits of access controls and privileges to ensure they remain appropriate over time. This includes reviewing user roles and access rights, especially after role changes, departures, or significant changes to systems or data classification.
- Educate and Train Employees: Training employees on the importance of access control, the proper handling of authentication credentials, and recognising phishing attempts are crucial for maintaining security. Awareness programs can significantly reduce the risk of security breaches due to human error.
Utilising Firewalls:
- Firewalls: are the cornerstone of effective access control, serving as a barrier that monitors and controls incoming and outgoing network traffic based on an organization's previously established security policies. Regular reviews and updates of firewall configurations are essential to adapt to new threats and ensure robust network perimeter security.
Access Control Technologies and Practices:-
- Physical Access Controls: Implement key cards, biometric scanners, and security personnel to control physical access to buildings and secure areas.
- Digital Access Controls: Use firewalls, encrypted VPNs, and secure gateways for controlling access to digital resources.
- Least Privilege Principle: Ensure users are granted the minimum levels of access – or permissions – needed to perform their job functions.
- Account Management Processes: Establish processes for creating, modifying, disabling, and deleting user accounts and access rights in a timely manner.
Monitoring and Responding to Access Control Violations:-
- Intrusion Detection Systems (IDS): Deploy IDS to monitor network and system activities for malicious activities or policy violations.
- Security Information and Event Management (SIEM): Use SIEM tools for real-time analysis of security alerts generated by applications and network hardware.
- Incident Response Plan: Have a plan in place that includes procedures for responding to unauthorised access attempts or breaches, including immediate containment strategies and communication protocols.
Pillar 3 - Incident Response Plan
An incident response plan is a structured approach for handling security breaches, attacks, or any unforeseen security incidents. It ensures that when an incident occurs, the response is swift, organised, and effective, thereby reducing the damage and preventing future breaches. Having a plan in place not only enhances an organization's resilience to cyber threats but also supports compliance with regulatory requirements and industry standards.

Developing a Comprehensive Incident Response Plan:-
- Establish an Incident Response Team (IRT): Form a team responsible for executing the incident response plan. This team should include members from various departments, such as IT, legal, HR, and communications, to cover all aspects of incident response.
- Preparation and Prevention: Regularly update and patch systems to prevent security vulnerabilities that could be exploited in a cyber-attack. Set up firewalls for controlling access and monitoring traffic to block unauthorised entry. Use comprehensive anti-malware tools for detection and real time prevention. Securely configure systems by disabling unnecessary services and changing default settings to reduce risks.Educating employees on these measures and their roles in cyber-security can significantly reduce the risk of incidents.
- Identify and Classify Incidents: Define what constitutes a security incident for your organisation and categorise incidents by severity levels. This will guide the response strategy and prioritisation.
- Incident Detection and Reporting: Implement mechanisms for detecting incidents and establish clear procedures for reporting them. This could include the use of intrusion detection systems (IDS), regular security audits, and encouraging a culture where employees feel empowered to report suspicious activities.
- Assessment and Analysis: Once an incident is detected and reported, assess its scope, impact, and the data/systems compromised. This assessment will inform the subsequent steps in the response process.
- Containment, Eradication, and Recovery: Develop strategies for containing the incident to prevent further damage, eradicating the threat from the organisation’s systems, and recovering affected systems and data. This may involve isolating affected networks, applying security patches, and restoring systems from backups.
- Communication: Outline communication protocols, including who should be notified internally and externally (such as law enforcement and affected clients), and when. Clear, timely communication can mitigate the reputational impact of an incident.
- Post-Incident Review: After managing an incident, conduct a thorough review to identify the cause, evaluate how it was handled, and determine what can be improved in the incident response plan. This step is crucial for learning from the incident and strengthening future responses.
Key Components of an Effective Incident Response Plan:-
- Roles and Responsibilities: Clearly define the roles and responsibilities of the IRT members.
Contact Information: Maintain an up-to-date list of contact information for IRT members and external entities (e.g., law enforcement, regulatory bodies). - Incident Logging and Documentation: Keep detailed records of the incident and the response to aid in post-incident reviews and compliance reporting.
- Legal and Regulatory Considerations: Understand and comply with legal and regulatory requirements related to incident reporting and data breaches.
Tools and Resources for Incident Response:-
- Forensic Tools: Utilise forensic tools to analyse incidents and gather evidence.
- Communication Tools: Have secure communication channels for coordinating the response to an incident.
- Data Backup and Recovery Solutions: Ensure that data backup and recovery solutions are in place and tested regularly.
Training and Simulations
Conduct regular training sessions for the IRT and all employees to familiarise them with the incident response plan and procedures. Simulate different types of incidents to test the effectiveness of the plan and the readiness of the team.
Pillar 4 - Regular Audits and Compliance
In the rapidly evolving digital landscape, maintaining a static cyber-security posture is insufficient. Regular audits and compliance checks are critical for identifying gaps in security defenses and ensuring that cyber-security measures remain effective against emerging threats. This pillar emphasizes the importance of continuous evaluation and alignment with legal and regulatory requirements, thereby safeguarding sensitive data and sustaining business integrity.
Implementing Regular Audits:-
Conducting regular security audits is a non-negotiable aspect of a robust cyber-security policy. These audits, both internal and external, serve to identify and rectify gaps in your cyber-security defenses, ensuring your measures are always aligned with the latest threats and compliance requirements.
-
Schedule Routine Security Audits: Establish a consistent schedule for conducting comprehensive security audits. These audits should assess all aspects of the organisation's cyber-security framework, from technical defenses to employee adherence to security policies.
-
Use of External Auditors: Consider engaging with external cyber-security auditors periodically. External auditors bring an unbiased perspective and can often identify vulnerabilities that internal teams might overlook.
-
Vulnerability Scanning and Penetration Testing: Regularly perform vulnerability scans and penetration tests to uncover and address security weaknesses. These tests simulate cyber-attacks to evaluate the effectiveness of security measures in real-world attack scenarios.
-
Review Access Controls: As part of the audit process, review user access levels to ensure that the principle of least privilege is strictly enforced. Verify that employees have access only to the resources necessary for their job functions.
- Secure Configuration: Secure configuration of all systems and devices minimizes the attack surface and prevents incidents. Regular compliance checks should verify that unnecessary services are disabled, unused ports are closed, and default credentials are altered. This process is vital in ensuring that all systems and devices are configured to the highest security standards, reducing vulnerabilities.
-
Patch Management: Integral to this pillar is the establishment of a rigorous patch management strategy. By regularly updating systems and applying necessary patches, you protect against vulnerabilities that could be exploited by cyber attackers.
-
Firewall Configuration Monitoring: Firewalls serve as a fundamental barrier, controlling inbound and outbound traffic and protecting the network from unauthorized access. Regular audits should include a thorough review of firewall configurations to ensure they are optimally set to manage and monitor traffic effectively. This process not only prevents unauthorized access but also identifies unusual activities that could signify a cyber threat.
-
Malware Protection: Incorporating malware protection into the regular audit process is crucial. This involves evaluating the effectiveness of current anti-malware solutions, ensuring they provide comprehensive scanning and real-time protection. Regular audits should assess the implementation of these solutions and their effectiveness in detecting and mitigating threats, alongside verifying that employees are trained to recognize potential malware.
Ensuring Compliance with Regulations:-
- Stay Informed on Regulatory Changes: Keep abreast of changes in cyber-security laws and regulations that affect your industry. This includes national laws, such as GDPR in the EU, and industry-specific regulations, like HIPAA for healthcare in the United States.
- Map Compliance Requirements to Security Controls: Align your cyber-security policies and controls with compliance requirements. This alignment helps in not just meeting regulatory mandates but also in enhancing the overall security posture.
- Data Protection and Privacy: Implement and regularly review measures to protect data privacy and integrity. This includes encryption, secure data storage solutions, and privacy impact assessments.
- Documentation and Reporting: Maintain thorough documentation of compliance efforts, security policies, audit results, and incident response activities. Proper documentation is crucial for demonstrating compliance during regulatory reviews and after security incidents.
Tools and Practices for Effective Audits and Compliance:-
- Automated Compliance Monitoring Tools: Utilise software that automates the monitoring of compliance with various standards and regulations. These tools can provide real-time alerts on non-compliance issues.
- Security Information and Event Management (SIEM) Systems: Deploy SIEM systems for continuous monitoring and analysis of security events. SIEM tools can help in identifying anomalies that may indicate compliance issues or security threats.
- Employee Training and Awareness: Regularly update training programs to include the latest compliance requirements and security best practices. Educated employees are less likely to inadvertently breach compliance or security protocols.
Challenges and Solutions in Audits and Compliance:-
- Keeping Up with Rapidly Changing Regulations: Establish a dedicated team or role responsible for tracking regulatory changes and updating internal policies accordingly.
- Resource Constraints: Small and medium enterprises (SMEs) may find regular audits and maintaining compliance challenging due to limited resources. In such cases, prioritising critical assets and leveraging automated tools can help manage the workload.
Pillar 5 - Employee Training and Awareness
The human element is often the weakest link in an organisation's cyber-security defenses. Phishing attacks, password breaches, and accidental data leaks are common issues that arise from a lack of awareness. Consequently, employee training and awareness programs are not just beneficial; they are essential components of a robust cyber-security strategy. These programs turn potential vulnerabilities into first lines of defense.

Developing Effective Training and Awareness Programs:-
- Assess Training Needs: Identify specific cyber-security knowledge gaps within your organisation. This assessment can be based on the types of data handled, employee roles, and previous security incidents.
- Create Engaging Content: Develop training materials that are engaging and relevant to your audience. Use a mix of formats, such as videos, interactive quizzes, and live workshops, to cater to different learning styles.
- Regularly Update Training Programs: Cyber-security threats evolve rapidly, and so should your training programs. Regular updates ensure that the content remains relevant and covers the latest threats, such as emerging phishing tactics or new malware types.
- Promote a Culture of Security: Beyond formal training sessions, foster an organisational culture that prioritises cyber-security. This can be achieved through regular communications, highlighting the importance of security in team meetings, and creating channels for employees to report suspicious activities without fear of reprisal.
- Simulate Cyber Threats: Conduct simulated phishing exercises and other threat simulations to provide practical experience. These exercises help employees recognise real-life threats and understand the importance of following security protocols.
Key Topics for Employee Training:-
- Phishing Recognition and Response: Teach employees how to recognise phishing emails and the steps to take when they encounter one.
- Password Security: Educate employees on creating strong passwords and the importance of using different passwords for different accounts.
- Handling Sensitive Data: Provide guidelines on how to handle and share sensitive information securely, including the use of encryption and secure file-sharing services.
- Mobile Device Security: Offer training on securing mobile devices that access corporate data, emphasising the importance of regular updates and the dangers of connecting to unsecured Wi-Fi networks.
- Incident Reporting Procedures: Ensure employees know how and when to report security incidents, emphasising that timely reporting can significantly reduce the impact of a breach.
Measuring the Effectiveness of Training Programs:-
- Feedback Surveys: After training sessions, collect feedback to gauge employee understanding and adjust future programs accordingly.
- Knowledge Assessments: Conduct pre- and post-training assessments to measure the knowledge gained and identify areas that need further clarification.
- Monitoring Phishing Simulations: Track the response to simulated phishing emails to identify trends, such as departments that may require additional training.
Challenges and Solutions in Cyber-security Training:-
- Engagement: Employees may view cyber-security training as uninteresting or irrelevant. Solution: Customise content to be role-specific and use interactive elements to increase engagement.
- Resource Constraints: Smaller organisations may lack the resources for comprehensive training programs. Solution: Leverage free or low-cost online training resources and prioritise training on the most critical threats.
Developing and Implementing a Cyber-security Policy
Developing and implementing a cyber-security policy is a critical step for SMEs to protect themselves against cyber threats. Here's a detailed approach to creating a robust cyber-security policy:
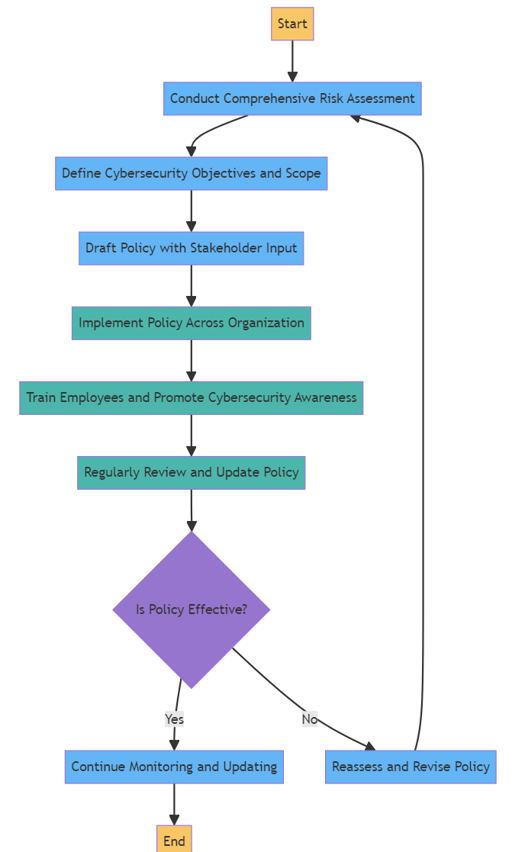
1 - Conduct a Comprehensive Risk Assessment
- Identify Digital Assets: Start by cataloging all digital assets within your organisation. This includes hardware, software, data, and any other resources involved in your IT infrastructure.
- Assess Threats and Vulnerabilities: Use the tools and methodologies discussed earlier and below to identify potential threats and vulnerabilities that could impact your digital assets. This should cover everything from malware and phishing attacks to system misconfigurations and unpatched software.
- Determine Impact: Evaluate the potential impact of each identified threat on your organisation, considering factors like data loss, financial damage, and reputational harm.
- Prioritise Risks: Based on the impact and likelihood of occurrence, prioritise the risks. This will help focus your cyber-security efforts on the most critical areas.
2- Define Your Scope and Cyber-security Objectives
- Outline the Scope: Clearly delineate the scope of your policy. Specify which assets, departments, and processes are covered. This ensures that all areas of your business are aware of their role in cyber-security.
- Set Clear Objectives: Define what your cyber-security policy aims to achieve. Objectives may include protecting customer data, ensuring system availability, and complying with regulatory requirements.
3- Draft the Cyber-security Policy with Key Stakeholder Input
- Engage Stakeholders: Involve stakeholders from across the organisation, including IT, human resources, legal, and executive teams. Their input will ensure the policy is comprehensive and aligned with business objectives.
- Outline Policy Elements: The policy should include sections on access control, incident response, data protection, and employee responsibilities, among others. Use clear, concise language that is accessible to all employees.
- Review and Revise: Draft the policy and circulate it among stakeholders for feedback. Revise the document as necessary to address any concerns or gaps.

4 - Implement the Policy Across the Organisation
- Communicate the Policy: Announce the new cyber-security policy through multiple channels to ensure it reaches all employees. This could include email announcements, company meetings, and postings on the internal company portal.
- Integrate into Daily Operations: Work with department heads to integrate the cyber-security policy into daily operations. This may involve updating existing processes or implementing new ones.
- Ensure Accessibility: Make sure the policy is easily accessible to all employees, such as through the company intranet or as a physical document in common areas.
5 -Train Employees and Promote Cyber-security Awareness
- Develop Training Programs: Create training programs that cover the key aspects of the cyber-security policy, as well as general cyber-security awareness. Tailor training sessions to different roles within the organisation for relevance.
- Promote a Security Culture: Encourage a culture of security within the organisation. This can include regular security tips in newsletters, posters highlighting security practices, and rewards for proactive security behaviors.
- Provide Resources: Offer resources for employees to learn more about cyber-security, such as access to online courses, webinars, and informative materials.
6 - Regularly Review and Update the Policy
- Schedule Reviews: Set a regular schedule for reviewing the cyber-security policy, at least annually or following significant changes to your IT environment or business operations.
- Adapt to Changes: Update the policy to reflect new cyber-security threats, technological advancements, and changes in regulatory requirements.
- Engage Stakeholders: Involve stakeholders in the review process to ensure the policy remains aligned with business objectives and operational practices.
By following these steps, SMEs can develop and implement a cyber-security policy that not only addresses current security needs but also adapts to future challenges, ensuring ongoing protection against cyber threats.
Leveraging Technology and Frameworks
Software Tools for Risk Assessment
Incorporating the right software tools into the risk assessment process can significantly enhance an organisation's ability to identify, analyse, and mitigate cyber-security risks. These tools offer automation, depth of analysis, and insights that manual processes cannot match. Below are key categories of software tools that are instrumental in conducting a comprehensive risk assessment, along with examples of popular options in each category.
Vulnerability Scanning Tools
Vulnerability scanners are essential for identifying security weaknesses in networks, systems, and applications. They automate the process of scanning for known vulnerabilities and provide reports detailing discovered issues.
- Nessus: One of the most widely used vulnerability scanning tools, Nessus is known for its comprehensive database of vulnerabilities and its ability to scan a wide range of environments, including cloud, mobile, and virtualised systems.
- Qualys: Offers cloud-based vulnerability management that scans and identifies vulnerabilities in your systems. It also provides continuous monitoring and web application scanning capabilities.
- OpenVAS: A free and open-source vulnerability scanner, OpenVAS is a powerful tool for conducting detailed vulnerability assessments. It's regularly updated with the latest tests and provides a robust framework for scanning networks.
Penetration Testing Tools
Penetration testing tools simulate cyber attacks against your computer system to check for exploitable vulnerabilities. These tools are used in conjunction with vulnerability scanners to validate the findings and assess the impact of potential breaches.
- Metasploit: An advanced open-source platform used for developing, testing, and executing exploit code against a remote target machine. It also offers insights for remediation and vulnerability validation.
- Burp Suite: A popular tool for web application security testing, offering a range of features from initial mapping to analysis of an application's attack surface, and exploitation of security vulnerabilities.
- Kali Linux: A Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing. It contains several hundred tools geared towards various information security tasks, such as Penetration Testing, Security Research, Computer Forensics, and Reverse Engineering.
Risk Management and Analysis Software
Risk management and analysis software helps organisations to assess, prioritise, and manage risks based on their severity and potential impact. These tools often include features for risk identification, assessment, mitigation planning, and reporting.
- RSA Archer: Provides a comprehensive suite of risk management tools that help organisations manage risks, demonstrate compliance, and automate business processes.
- LogicManager: A cloud-based risk management software that offers solutions for identifying, assessing, and monitoring risks, with customisable frameworks and reporting capabilities.
Compliance Management Tools
Compliance management tools help ensure that organisations meet industry standards and regulatory requirements, which is a critical component of the risk assessment process.
- ComplianceForge: Offers comprehensive compliance documentation and templates that help organisations align their cyber-security measures with industry standards and regulations.
Selecting the right mix of tools depends on various factors, including the size of the organisation, the complexity of the IT infrastructure, and specific industry requirements. By leveraging these software tools, organisations can enhance their risk assessment processes, gaining deeper insights into their security posture and more effectively prioritising their cyber-security efforts.
The Cyber Essentials Scheme
Incorporate the Cyber Essentials scheme into your cyber-security strategy. This government-backed framework provides a clear structure for enhancing IT security and can serve as a guideline for compliance and certification efforts.

A Proactive Step Towards Cyber Resilience
Cyber Essentials is a pivotal certification that arms you with crucial defenses against a broad spectrum of common cyber attacks. This certification is especially vital as it shields against basic attacks, which are often precursors to more sophisticated threats. Achieving this certification assures that your organization has implemented core technical controls to repel the majority of cyber attacks.
The Pathway to Certification
The certification process is centered around a self-assessment of five fundamental security controls, verified by an independent assessor. This assessment, streamlined through a secure, user-friendly platform, ensures a seamless certification journey.
Scope of Cyber Essentials
Understanding the scope is critical for effective certification. The scheme requires the inclusion of your entire IT infrastructure or a clearly defined subset, ensuring comprehensive coverage. This inclusivity is strategic, offering robust protection and enhancing customer confidence in your security posture.
The Five Key Controls of Cyber Essentials
- Firewalls: Essential for restricting access to safe and necessary network services from the Internet, ensuring that only authorised services are accessible.
- Secure Configuration: Devices and software must be correctly set up to minimise vulnerabilities, including the removal of unnecessary software and user accounts.
- User Access Control: Access should be restricted to those who need it, with strong authentication methods in place to verify user identities.
- Malware Protection: Mechanisms must be in place to detect and remove malware, with regular updates to anti-malware software.
- Security Update Management: Ensures that devices and software are up-to-date, protecting against known vulnerabilities.
Implementing Cyber Essentials Controls
Implementing these controls involves assessing your current firewall configurations, ensuring devices are securely configured, managing user access effectively, establishing robust malware protection, and managing security updates diligently.
Preparing for Cyber Essentials Certification
Understanding the certification requirements and completing the online assessment are crucial steps. Choose a reputable certification body and familiarise yourself with the assessment process. Documentation and evidence of compliance with Cyber Essentials controls will be necessary for the assessment.
Benefits of Cyber Essentials
- Compliance and Competitive Advantage: Demonstrates your commitment to cyber-security, offering a competitive edge.
- Cost-Effective Risk Management: Focuses on the most common threats, allowing for efficient resource allocation.
- Business Continuity: Ensures operations continue smoothly, safeguarding against disruptions from cyber incidents.
Integrating Cyber Essentials into Your Cyber-security Policy:
Incorporating the Cyber Essentials scheme into your cyber-security policy development process involves:
- Mapping Cyber Essentials Controls to Policy Pillars: Identify how each Cyber Essentials control corresponds to the actions and measures outlined in your cyber-security policy pillars. This ensures a holistic approach that covers all aspects of cyber-security.
- Leveraging Cyber Essentials for Compliance: Use the scheme’s framework as a guide for compliance checks within your policy. This not only aids in meeting regulatory requirements but also in achieving and maintaining Cyber Essentials certification.
- Enhancing Policy with Cyber Essentials Resources: Utilise the tools, checklists, and guidance provided by the Cyber Essentials scheme to enrich the content and effectiveness of your cyber-security policy, providing a practical roadmap for implementation and improvement.
- By integrating the Cyber Essentials criteria into the fabric of your cybersecurity policy, you create a synergistic approach that enhances your SME’s defense against cyber threats. This alignment not only streamlines compliance and certification processes but also elevates the overall security posture of your organisation, ensuring that you are well-equipped to navigate the complexities of the digital landscape.
Conclusion
Implementing a cyber-security policy is not merely a regulatory necessity but a strategic imperative for SMEs in the UK and beyond. In an era where digital threats are increasingly sophisticated and pervasive, having a robust cyber-security framework is the cornerstone of trust, reliability, and business continuity. This guide has walked you through the essential steps to develop and implement a comprehensive cyber-security policy, emphasising the importance of regular updates and employee training to navigate future challenges successfully.
Cyber-security is a collective responsibility, extending beyond the IT department to every employee. By cultivating a culture of security awareness and vigilance, you significantly enhance your defenses against cyber threats. We encourage you to utilise the software tools and methodologies outlined in this guide to strengthen your risk assessment processes and tailor your cyber-security policy to meet your business's unique needs and challenges. By doing so, you not only protect your digital assets and customer data but also safeguard your reputation and secure your enterprise's long-term success.
Stay proactive, stay informed, and remember, in the realm of digital operations, your cyber-security policy is your most potent shield. Let it be robust, comprehensive, and reflective of industry best practices. For more insights and guidance on mastering cyber-security complexities, engage with our social media content and join a community dedicated to cyber-security excellence.
For More Information Please Contact Us

ACCREDITATIONS






