What Is Cyber Essentials?
In today's rapidly changing cyber-security landscape, it's more important than ever for businesses to strengthen their defenses against a growing array of cyber threats. The UK's Cyber Essentials Scheme, a government-backed and industry-supported framework, offers organisations of all sizes a robust approach to securing their IT infrastructure. This comprehensive guide will explore the scheme's intricacies, its benefits, and the pathway to compliance.

Table of Contents
- What Is Cyber Essentials?
- A Proactive Step Towards Cyber Resilience
- What Does Cyber Essentials Cover?
- What are the Five Controls of Cyber Essentials?
- Practical Steps for Implementing Cyber Essentials Controls
- Preparing for Cyber Essentials Certification
- Benefits of Cyber Essentials
- Is Cyber Essentials Worth Having?
- Conclusion: Embracing Cyber-security Excellence
A Proactive Step Towards Cyber Resilience
Cyber Essentials is an independently verified self-assessment certification that equips your organisation with essential protection against a wide range of common cyber attacks. This is crucial, as being vulnerable to basic attacks can expose you to more advanced and targeted cyber threats.
Achieving certification under the Cyber Essentials Scheme provides the assurance that your defenses are equipped to thwart the majority of common cyber attacks. These attacks often seek out targets lacking essential technical controls – a gap that Cyber Essentials aims to address.
The process involves a self-assessment against five fundamental security controls, which is then verified by a qualified assessor. The self-assessment is facilitated through a secure, hosted platform powered by the Cyber Essentials assessment platform. This platform, featuring Pervade’s intuitive user interface, allows for a straightforward and efficient assessment experience.
By adopting the Cyber Essentials Scheme, organisations not only enhance their cyber-security posture but also demonstrate a commitment to best practices in IT security – an increasingly vital aspect in today's digital world.
What Does Cyber Essentials Cover?
Understanding the scope of the Cyber Essentials scheme is essential for its effectiveness and applicability. For any organisation seeking certification, understanding and accurately defining this scope is the first step towards achieving Cyber Essentials.
Scope Inclusivity
The Cyber Essentials scheme requires that the assessment and certification encompass the entire IT infrastructure of the applicant organisation. This includes all devices, networks, and software that are integral to conducting business operations. Alternatively, a well-defined and separately managed subset of the IT infrastructure can also be considered, provided its boundaries in terms of business unit, network, and physical location are clearly delineated.

The Importance of Comprehensive Coverage
Opting for a scope that includes the entire IT infrastructure is not just a requirement but a strategic move. It ensures the best protection against cyber threats and bolsters customer confidence in the organisation's commitment to data security.
Criteria for Devices and Software
The Cyber Essentials requirements apply to all devices and software within the defined scope, particularly those that:
- Accept incoming network connections from untrusted, Internet-connected hosts.
- Establish user-initiated outbound connections to the Internet.
- Control the flow of data between devices and the Internet.
Non-Exclusion of End-User Devices
A crucial aspect of the scope is the inclusion of end-user devices. Any scope that excludes these devices is deemed unacceptable for Cyber Essentials certification. This underscores the importance of comprehensive security measures that encompass all aspects of an organisation's IT infrastructure.
What are the five controls of Cyber Essentials?
The Cyber Essentials scheme is built upon five fundamental technical security controls, each being designed to address specific vulnerabilities within an organisation's IT environment. Understanding and implementing these controls is crucial for any organisation aiming to comply with the scheme and bolster its cyber-security posture.
Firewalls
Objective:
Ensure only safe and necessary network services are accessible from the Internet.
Introduction:
Devices run network services that communicate with other devices and services.
Restricting access to these services via firewalls or equivalent network devices reduces exposure to attacks.
Requirements:
All in-scope devices must have a properly configured firewall.
Change default administrative passwords or disable remote administrative access.
Block unauthenticated inbound connections by default.
Approve and document inbound firewall rules.
Remove or disable unnecessary firewall rules promptly.
Use software firewalls on devices used in un-trusted networks.

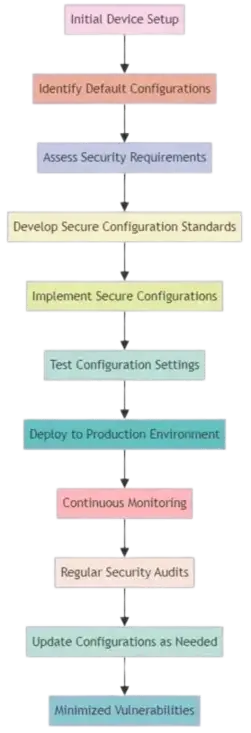
Secure Configuration
Objective:
Ensure computers and network devices are properly configured to minimise vulnerabilities.
Introduction:
Default configurations often include weak points like predictable passwords or run unnecessary services.
Requirements:
Actively manage and configure computers and network devices.
Remove unnecessary user accounts and software.
Disable auto-run features for file execution.
Ensure user authentication before accessing organisational data.
User Access Control
Objective:
Ensure user accounts are assigned appropriately and provide only necessary access.
Introduction:
Managing user accounts and privileges is key to preventing unauthorized access and data breaches.
Requirements:
Have a user account creation and approval process.
Authenticate users with unique credentials.
Implement Multi-Factor Authentication (MFA) where available.
Remove or disable user accounts when no longer needed.

Malware Protection
Objective:
Restrict execution of known malware and untrusted software to prevent damage or access to sensitive data.
Introduction:
Malware, including viruses, worms, and spyware, can cause significant harm. It's essential to have mechanisms in place to detect and disable malware.
Requirements:
Implement malware protection mechanisms on all in-scope devices.
Use anti-malware software with up-to-date signature files.
Employ application allow listing and sand-boxing to control software execution.

Security Update Management
Objective:
Ensure devices and software are not vulnerable to known security issues for which fixes are available.
Introduction:
Regularly updating software is crucial to protect against vulnerabilities that could be exploited by attackers.
Requirements:
Keep all software on in-scope devices licensed, supported, and up-to-date.
Apply updates, especially those addressing critical or high-risk vulnerabilities, within 14 days of release.
Enable automatic updates where possible.
Conclusion of Technical Security Controls
Understanding and implementing these technical security controls is fundamental to achieving Cyber Essentials certification. Each theme plays a vital role in forming a comprehensive cyber-security strategy that aligns with the scheme's objectives. By adhering to these guidelines, organisations not only comply with the Cyber Essentials scheme but also significantly strengthen their defense against a wide array of cyber threats.
Practical Steps for Implementing Cyber Essentials Controls
After understanding the technical security controls of the Cyber Essentials scheme, the next crucial step is their practical implementation. This section provides guidance on how to effectively apply these controls within your organisation.
Implementing Effective Firewall Management
Assessment of Current Firewall Configuration:
Begin by assessing the current state of your firewalls. Ensure that they cover all in-scope devices and that their rules are up-to-date and relevant to your business needs.
Regular Review and Update of Firewall Rules:
Establish a routine for reviewing and updating firewall rules. This includes removing outdated rules and ensuring that any changes in your network are reflected in your firewall configurations.
Ensuring Secure Configuration of Devices
Develop a Standard Configuration Policy:
Create a policy for the secure configuration of all new devices. This should include disabling unnecessary services, changing default passwords, and enabling security features.
Regular Audits and Updates:
Conduct regular audits of device configurations to ensure compliance with your policy. Update these configurations in response to new threats or vulnerabilities.
Strengthening User Access Controls
Review and Rationalize User Accounts:
Regularly review user accounts to ensure that each account is necessary and has appropriate access levels.
Implement and Enforce MFA:
Wherever possible, implement Multi-Factor Authentication. This adds an extra layer of security, particularly for administrative accounts or accounts with access to sensitive data.

Establishing Robust Malware Protection
Deploy and Maintain Anti-Malware Solutions:
Ensure that anti-malware software is installed on all in-scope devices and that it is regularly updated.
Educate Users on Safe Practices:
Regularly educate users about the risks of malware and the importance of safe practices, such as not downloading un-trusted applications.

Managing Security Updates Effectively
Automate Software Updates Where Possible:
Utilize automated update features to ensure that software is always up-to-date.
Establish a Patch Management Process:
Develop a process for tracking and applying critical security patches, ensuring that they are deployed within the recommended time frame.
Preparing for Cyber Essentials Certification
Having implemented the necessary technical security controls, the next step is to navigate the certification process for Cyber Essentials. This section outlines the key stages and provides tips for a successful certification journey.
Understanding the Certification Requirements
Familiarise with the Criteria:
Ensure you have a thorough understanding of the Cyber Essentials requirements. Review the official guidelines and any updates to the scheme.
Documentation and Evidence:
Prepare the necessary documentation and evidence demonstrating compliance with the Cyber Essentials requirements. This documentation and evidence will be uploaded as part of the online assessment.
Self-Assessment Checklist/Toolkit:
Utilise the self-assessment checklist/toolkit provided by the Cyber Essentials scheme to gauge your readiness.

Completing the Cyber Essentials online Assessment
Choosing a Certification Body:
Choose a certification body accredited by the UK's National Cyber Security Center (NCSC) like ProCheckUp. Ensure that like ProCheckUp they have a good reputation and can provide the necessary support.
Understanding the Assessment Process:
Discuss with the chosen certification body their assessment process, timelines, and any support they offer during the certification journey.
Online Certification Assessment
Complete the online Certification Assessment logging in with the provided credentials
Post-Certification Actions
Receiving Certification:
Once certified, publicise your achievement to stakeholders and customers to enhance trust and market reputation.
Continuous Improvement:
Treat certification not as an endpoint but as a step in ongoing cyber-security improvement. Regularly review and update your security measures.
Benefits of Cyber Essentials
The Cyber Essentials scheme provides a robust framework for organizations to bolster their cyber-security defenses. By adhering to its guidelines, businesses can significantly reduce their vulnerability to a wide range of common cyber attacks. This enhanced security posture is not just about preventing breaches; it's about building a foundation of trust with customers and stakeholders.

Compliance and Competitive Advantage
Compliance with the Cyber Essentials scheme is more than a regulatory checkbox. It positions your organisation as a trusted and secure entity in a landscape where data breaches are increasingly common. This compliance can be a unique selling point, setting you apart from competitors who may not prioritize cyber-security as highly.
Cost-Effective Risk Management
Implementing the Cyber Essentials controls is a cost-effective approach to risk management. By focusing on the most common threats, businesses can allocate their resources more efficiently, avoiding the need for expensive, complex solutions that may not address their most pressing vulnerabilities.
Continued Business Continuity
Cyber Essentials helps ensure that your business operations are not disrupted by cyber incidents. This continuity is crucial for maintaining customer trust and avoiding the significant costs associated with downtime and data loss.
Is Cyber Essentials Worth Having?
Deciding whether Cyber Essentials is worth having depends on several factors, including the nature of your business, the sensitivity of the data you handle, and your overall exposure to cyber risks. However, for most organizations, the benefits of obtaining Cyber Essentials certification can be substantial:
-
Enhanced Reputation: Cyber Essentials certification can boost your organisation's reputation by demonstrating a commitment to cyber-security. This can be particularly beneficial when dealing with clients or partners who are sensitive to data security.
-
Reduced Insurance Costs: Many insurers recognize the value of the Cyber Essentials certification and may offer lower premiums on cyber insurance as a result.
-
Compliance with Contractual Requirements: Increasingly contracts, especially those involving government bodies, require suppliers to have the Cyber Essentials certification. Cyber Essentials certification fulfills this requirement and open up new business opportunities.
-
Focused Cyber-security Strategy: The framework helps businesses focus their cyber-security efforts on critical areas, which can be more effective than a scattered approach. This targeted strategy helps in prioritizing investments in security technologies and practices.
-
Baseline Security: It provides a baseline of cyber-security measures that are recognised across various industries. This baseline helps businesses establish a minimum acceptable level of security that can serve as a foundation for further enhancements.
Conclusion: Embracing Cyber-security Excellence
Achieving Cyber Essentials certification is a significant milestone in any organisation's cyber-security journey. It demonstrates a commitment to protecting against cyber threats and enhances trust among customers and partners. Remember, the journey doesn't end with certification; it's a continuous process of improvement and adaptation to the evolving cyber landscape.
For More Information Please Contact Us

ACCREDITATIONS






