It is undeniable that the sophistication of security technologies such as EDR, next-generation firewalls, IPS/IDS, etc. have grown significantly over the years to combat cyber-attacks. However, these technologies haven’t had a good rate of success when it comes to stopping or preventing attacks. People might blame the lack of proper detection programs or configuration etc. Depending completely on a signature-based detection approach is no longer sufficient considering the evolution of attack techniques and the magnitude of cyber-attacks being carried out. This is where Cyber Threat Intelligence comes into the picture.
Cyber Threat Intelligence or CTI is a division or discipline in cyber security that deals with the collection, processing, and analysing of threat data to understand a threat actor’s motives, target, and attack behaviours. Better knowledge about cyber threats gives the latest threat trends on the cyber threat landscape and better anticipates cyber-attacks.
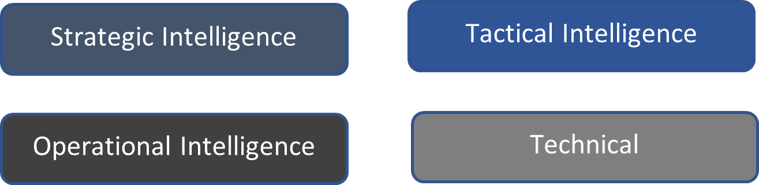
CTI falls into four categories:
In short,
- Strategic Intelligence – High-level execs. and management
- Operational Intelligence – Information on incoming specific threats/attacks
- Tactical Intelligence – Information regarding attackers’ TTPs/More automated
- Technical Intelligence – Indicator of Compromise, Signatures, etc.
Strategic intelligence is nothing more than high-level information that can be used by the non-technical audience such as the management and high-level executive members. Whitepapers, policy documents, and publications are some examples of strategic Cyber Intelligence.
Operational Intelligence focuses on seeking to answer “how” and “where” the attacks could happen. Anticipating attacks is one of the key areas to enable security analysts to visualise and predict the techniques used by attackers. Obtaining the attack knowledge can provide detailed insights into factors such as nature, motivation, timing, and attack methods. Ideally, information is collected through penetration from hacker chat rooms or online discussions, which is difficult to obtain. In short, operational CTI provides a coherent framework to analyse and prioritise potential threats and vulnerabilities in the organisation’s threat environment, thereby linking the possibility and impact of cyber-attacks to their strategic implications.
Tactical Intelligence is focused more on “Tactics, Techniques, and Procedures (TTPs)”. It also examines what is happening in an organisation’s network, focusing on the strengths and weaknesses of an organisation’s network defences. Tactical Intelligence also seeks to identify how a threat actor plans to attack an organisation and match that with detection and mitigation strategies. Examples of Tactical CTI are malware signatures, IP and URL blacklists, traffic patterns, log files, and credentials found in APT, ransomware, and phishing campaigns. Tactical Intelligence can be automated which means it utilises big data to analyse threat data and present its findings to analysts to further verify the results. This has the potential to shorten the manual analysis time and could allow for a timely and accurate response should an incident is to happen.
Technical Intelligence shares some similarities with Tactical Intelligence in some ways when identifying a threat actor’s TTPs, however, technical intelligence goes further into the core details of threat data and information such as IOCs, etc. and makes use of the technical data and put into security operations for network monitoring for malicious activity. Examples of technical CTI include malicious endpoint IP addresses and domains, phishing email headers, malware hash checksums, and so on. Meanwhile, the threat hunting team can benefit from this as it would narrow down the focus toward specific threats in a specific area where attackers might have compromised.
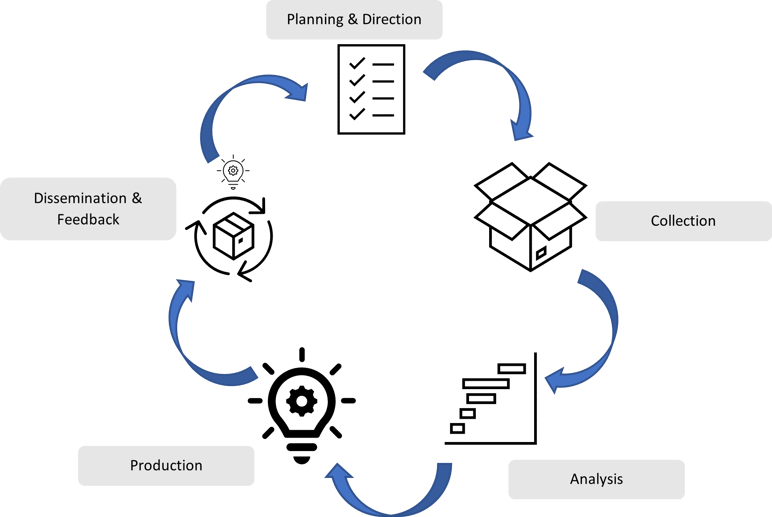 Figure 2: Threat Intelligence Lifecycle
Figure 2: Threat Intelligence Lifecycle
In order to maintain a strong Threat Intelligence program, a good threat intelligence lifecycle must be in place as this will ensure the operation of threat intelligence is always up and running and reliable in terms of the confidence of collected intelligence. To achieve this, a good threat intelligence lifecycle has the following stages:
- Planning & Direction
- Collection
- Analysis
- Production
- Dissemination & Feedback
Stage 1: Planning & Direction
The first step of anything is always planning. Planning and scoping the requirements of a good threat intelligence program is essential. This would give clear visibility to the main goals and tasks for your threat intelligence program.
Key considerations during planning:
-
- Which types of assets, personnel, and processes are at risk?
- How will threat intelligence improve operational efficiency?
- What other applications/systems could benefit from it?
Stage 2: Data Collection
Data quantity and quality are both critical components of the threat intelligence collection stage. If you veer astray with either quantity or quality, your organisation could be inundated with false positives, or you miss serious threat events.
Intelligence collection establishes the scope of your sources, both in terms of the data volume and type. This includes a wide range of threat types like phishing, compromised credentials, network logs, common vulnerabilities, and exploits (CVEs), leaked malware variants, and far more malicious activity generated by threat actors.
The processing component of phase two then seeks to normalise, structure, and deduplicate all the amassed data. Specific processing procedures often include reducing the volume of raw data, translating conversations obtained from foreign-language dark web marketplaces and illicit forums, and metadata extraction from malware samples.
Key considerations during data collection:
-
- Where are your current internal and external blind spots?
- What technical and automated collection techniques can you employ?
- How well can you infiltrate cybercriminal forums and closed sources on the dark web?
Stage 3: Data Analysis
After raw data have been gathered and stored in a centralised repository, they can be analysed next, and it is mostly a qualitative and often human-oriented process aimed. It is aimed at contextualizing processed threat intelligence through the enrichment and application of known structural data or advanced correlation and data modelling.
Stage 4: Production
At this stage, the data analysis work is now complete and ready to be put into production. This stage focuses on the efforts of development of arranging finished intelligence into easy-to-digest graphical charts, dashboards, and reports. During production, it’s essential to identify the most meaningful information and derive logical conclusions from the data and analysis completed in the prior phase.
Recommendations that outline appropriate courses of action will often include prepared decision trees and procedures to initiate incident and ransomware response, threat remediation, and patch management, among many others.
Based on the finished intelligence, production stakeholders finalise reports and prepare the communications to the final team members and key decision-makers. Ultimately, this final audience of the finished threat intelligence will assess the analysis and decide whether to take action.
Key considerations when obtaining processed and analysed intelligence:
-
- What are the most important findings of the analysis, and what’s the best way to illustrate them?
- Is the analysis reliable, relevant, and accurate?
- Are there clear and concrete recommendations or next steps regarding the end analysis?
Stage 5: Dissemination & Feedback
In order to drive results and address the risks, the security teams must distribute their finished intelligence reports to the appropriate stakeholders so that they can evaluate the findings, make key decisions, and provide feedback to continually refine intelligence operations. At the same time, this feedback is also going to help with the improvements in speed and efficiency of intelligence activities and the time to reach final delivery.
Key considerations:
-
- Which stakeholders benefit from finished threat intelligence reporting?
- What is the best way to present the intelligence and at what delivery frequency?
- How valuable is the finished intelligence? How actionable is it, and does it enable your organisation to make informed security decisions?
Intelligence Sources
In the Cyber Intelligence community, threat intelligence is often shared among the security communities where information and threat data from sensors can be exchanged and analysed and ultimately allows for better preparation and response against incoming cyber-attacks.
Threat Intelligence sources:
-
- Open-source intel – OSINT
- Closed-source intel – FS-ISAC etc.
- Cyber-threat feed – AlienVault, Cisco Talos, Honeypots, etc.
- Threat Intel. Exchange platforms – IBM X-Force Exchange, VirusTotal, etc.
Threat feeds are a valuable way to gather information regarding adversaries and their capabilities and infrastructure. Threat feeds are made up of a large quantity of data but are usually not intelligence. Threat Intelligence Feeds are actionable threat data related to artefacts or indicators collected from any third-party vendors to learn from other companies’ visibility and access to enhance your cyber threat response and awareness. Threat Intelligence Feeds concentrate on a single area of interest. The caveat of having threat feeds and other intelligence sources is that it needs to be tailored according to the nature of an organisation’s business. For example, the healthcare sector may not benefit from an intelligence source from FS-ISAC since it is made specifically for the Financial sector and does not contain intelligence related to a campaign for example, where attackers are going after patients’ records, etc.
Threat Intelligence Supports Incident Response
Threat Intelligence has a lot of applications and one of them is in the Incident Response arena!
 Figure 3: Threat Intelligence Feed
Figure 3: Threat Intelligence Feed
Data breaches happen all the time! Large corporations such as Target (reported data breach in 2013) were most probably one of the biggest data breaches in history with about 40 million credit and debit card information and 70 million customer records stolen.
In the event of a data breach, it is important for an organisation to know how to respond to it. It is all about preparation for when a cyber incident goes awfully wrong, you can respond faster and minimise the damage that is done to your business, your customers, your brand, etc.
The traditional mindset of threat intelligence is that the practice is used exclusively at the tactical level by defenders, but recently we’re starting to see more use cases of strategic and operational level CTI being plugged into incident response.
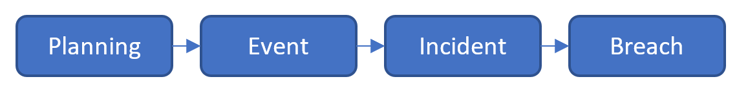
Figure 4: A graphical flow of a breach happened
We will be focusing on where a breach has occurred and how threat intelligence plays its part in Incident Response.
Assuming for the worst, an event escalates into an incident if it is determined that an adversary established a level of presence within the environment. In the event of an incident can not be contained, it could lead to a breach. Typically, this occurs when data exfiltration has occurred, and the organisation must report it to regulators, customers or employees.
Post-mortem on a breach is another place where strategic and operational Threat Intelligence plays an important role to determine:
-
- What happened?
- How did it happen and why?
- To investigate and find out the possible solutions through Forensics, etc.
Operational threat intelligence puts the incident through the lens of the Threat Triangle – what is the adversary’s capability, intent, and opportunity. Armed with this intel, this will not only greatly assist in the investigation of the breach but also assist in the remediation work based on what has been learned so the breach can be prevented in the future.
Find out more about Incident Response services with ProCheckUp.
Nonetheless, having a good threat intelligence program incorporated with the business not only increases the incident preparedness but also plays one of the major parts in cyber resilience.
“If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.” – a beautiful yet wise quote by Sun Tzu, The Art of War.
References:
-
- https://socradar.io/what-is-technical-cyber-threat-intelligence-and-how-to-use-it/
- https://www.securitymadesimple.org/cybersecurity-blog/best-cyber-threat-intelligence-sources-2021
- https://cofense.com/difference-between-threat-feeds-and-threat-intelligence-feeds/
- https://www.fsisac.com/
- http://procheckup.com/services/incident-response/
- https://www.recordedfuture.com/threat-intelligence-lifecycle-phases/
- https://www.securityweek.com/using-cyber-threat-intelligence-support-incident-response



Categories